When you sign into your online accounts – a process we call “authentication” – you’re proving to the service that you are who you say you are. Traditionally that’s been done with a username and a password. Unfortunately, that’s not a very good way to do it. Usernames are often easy to discover; sometimes they’re just your email address. Since passwords can be hard to remember, people tend to pick simple ones, or use the same password at many different sites.
That’s why almost all online services – banks, social media, shopping and yes, Microsoft 365 too – have added a way for your accounts to be more secure. You may hear it called “Two-Step Verification” (2FA) or “Multifactor Authentication” (MFA) but the good ones all operate off the same principle. When you sign into the account for the first time on a new device or app (like a web browser) you need more than just the username and password. You need a second thing – what we call a second “factor” – to prove who you are.
Why Use MFA?
Cybercriminals have more than 15 billion stolen credentials to choose from. If they choose yours, they could take over your bank accounts, health care records, company secrets, and more.
Multi-factor authentication is important, as it makes stealing your information harder for the average criminal. The less enticing your data, the more likely that thieves will choose someone else to target.
As the name implies, MFA blends at least two separate factors. One is typically your username and password, which is something you know. The other could be:
- Something you have. A cellphone, keycard, or USB could all verify your identity.
- Something you are. Fingerprints, iris scans, or some other biometric data prove that you are who you say you are.
Adding this secondary factor to your username/password protects your privacy. And it’s remarkably easy for most people to set up.
Do Passwords Offer Enough Security?
We all use passwords to gain entry into our email systems, work databases, and bank accounts. We are usually forced to change our combinations periodically in the hopes that we’ll stay just a bit safer. But the truth is that, on their own, passwords no longer provide an appropriate level of security.
Consider Google & Microsoft. One password gives access to:
- Email. The messages you’ve sent, those you’ve received, and the accounts you talk to are all stored in the system and protected with only a password.
- Calendars. Information about who you’ve met, where you were, and what you did are all linked to a password.
- Other web apps. Use your Google or Microsoft account to connect to other online resources, such as Hootsuite or Salesforce, and your password could reveal a great deal of data.
In 2017, Google reported that hackers steal almost 250,000 web logins each week. In 2019 Breach Alarm reported this number had increased to 1 million each week and the number is expected to be considerably higher today.
When we think about data breaches, we often think about personal bank accounts and lost money. But businesses, especially poorly secured small businesses, are a huge target. By gaining access to your email system, threat actors can portray themselves as a leader in your organization getting employees to serve on their behalf.
Companies are recognizing these risks and acting accordingly. Most enterprise organizations now require MFA as standard practice.
How Does MFA Work?
Most MFA systems won’t eliminate usernames and passwords. Instead, they layer on another verification method to ensure that the proper people come in and the thieves stay out.
A typical MFA process looks like this:
- Registration: A person links an item, such as a cellphone or a key fob, to the system and asserts that this item is theirs.
- Login: A person enters a username and password into a secure system.
- Verification: The system connects with the registered item. Phones might ping with verification codes, or key fobs might light up.
- Reaction: The person completes the process with the verified item. Entering verification codes or pushing a button on a key fob are common next steps.
Some systems demand this verification with each login, but some systems remember devices. If you always use the same phone or computer to log in, you may not need to verify each visit. But if you attempt to log in on a new computer or during an unusual time of day, verification might be required.
MFA may seem simple, but it’s remarkably effective. Microsoft says, for example, that MFA blocks 99.9% of account hacks. This one tiny step could protect your security in a huge way.
What does MFA look like for Microsoft 365?
Let’s say you’re going to sign into your work or school account, and you enter your username and password. If that’s all you need then anybody who knows your username and password can sign in as you from anywhere in the world!
But if you have multifactor authentication enabled, things get more interesting. The first time you sign in on a device or app you enter your username and password as usual, then you get prompted to enter your second factor to verify your identity.
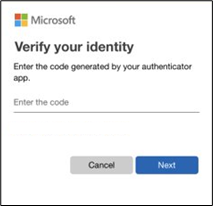
Perhaps you’re using the free Microsoft Authenticator app as your second factor. You open the app on your smartphone, it shows you a unique, dynamically created 6-digit number that you type into the site and you’re in.

If somebody else tries to sign in as you, however, they’ll enter your username and password, and when they get prompted for that second factor they’re stuck! Unless they have YOUR smartphone, they have no way of getting that 6-digit number to enter. And the 6-digit number in Microsoft Authenticator changes every 30 seconds, so even if they knew the number you used to sign in yesterday, they’re still locked out.
Next steps
Most cloud based systems (software you use with a web browser) offer multi-factor authentication these days. Even if your systems are emailing or texting you for verification already, Lean On Me I.T. recommends you upgrade to the authentication app method for a higher level of security. For business systems, contact your IT team and/or software vendors to see how you can implement multi-factor authentication. For personal use, check your email provider, banking systems and other accounts that may contain sensitive data to setup MFA. The great news is that whether you choose Microsoft Authenticator or another app, one app can manage the MFA codes for all of your systems.